Posted on: 16 August, 2018 - 10:30
The Guest Wireless service is available for AUS visitors, guests, and conference attendants. Below are instructions on how to connect to the Guest Wireless network.
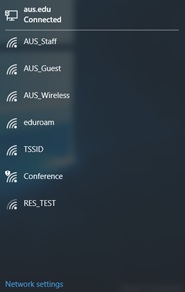
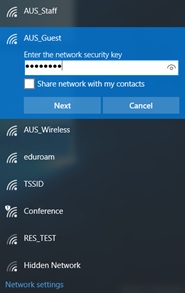
Step 1: Connect to AUS_Guest wireless network. Please approach the IT Service Desk or Technical Support team in the academic areas to get the password required for this step.
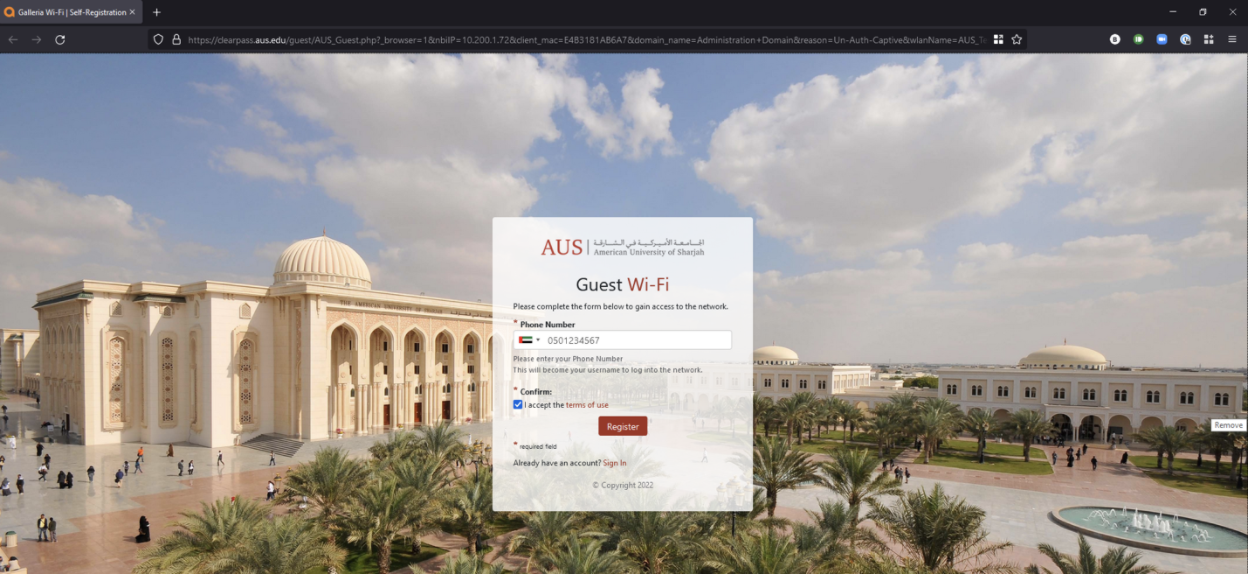
Step 2: Enter your mobile number to receive a voucher code via SMS. Review and accept the Terms and Conditions, then click on "Register".
Step 3: Enter the voucher code received via SMS and click "Log In".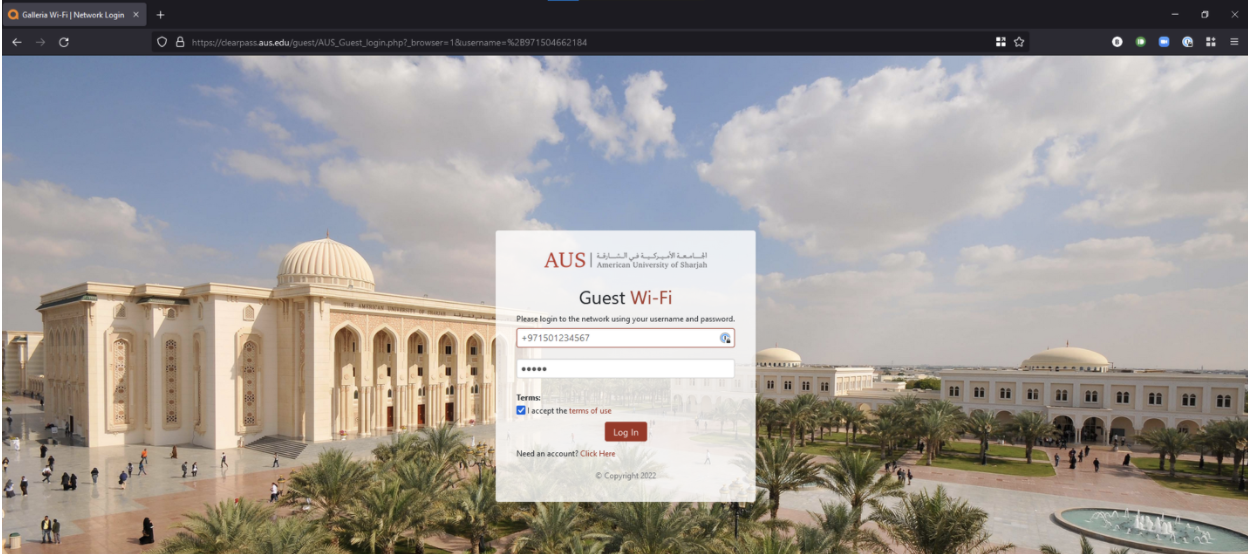
Step 4: Your enrollment is complete. No additional steps are required and you should now be connected to the Internet.
NOTE: The voucher code is valid for 7 days and can be used for up to two devices.
Terms and Conditions:
- In order to comply with certain local laws and regulations, access to some online content will be either limited or unavailable. This includes, but is not limited to, a number of social media and video streaming websites.
- Guest Wireless service is available for non-AUS users.
- AUS students or employees should not use Guest Wireless service; instead, they should use their own credentials to login to their designated wireless networks. Instructions on how students and employees can access the wireless networks are also available on the ITFAQ website at https://itfaq.aus.edu.
- By accessing the “AUS_Guest” wireless network, users agree that they will adhere to the AUS IT policies as published on our website at https://www.aus.edu/IT.
- By accessing the “AUS_Guest” wireless network, users consent to and acknowledge that they are aware that all data transiting the University network or stored on university computers may be monitored, recorded and examined in furtherance of these objectives. Data may only be disclosed to law enforcement or other officials as required by UAE law, AUS policy and other legal obligations.
- The Chancellor, Chief Operating Officer and Provost will be considered authorized persons for purposes of disclosing any AUS data to external officials, or initiating investigations that would require more detailed examination or monitoring of data. More detailed examination will be considered activities beyond the routine monitoring necessary for the good operation of AUS systems and networks
